Bug Bounties Hit Limits as AI Puts Crypto Hackers on Equal Footing
At Token2049, Immunefi CEO Mitchell Amador highlighted a growing concern in crypto security: the rise of AI-driven hacks. He explained that artificial intelligence is now being used not only for defensive audits but also for offensive attacks. This shift is accelerating the pace at which vulnerabilities are found and exploited, leaving less time for teams to respond effectively.
Amador emphasized that the traditional bug bounty model is struggling to keep up with this new reality. Where once there was a safer buffer between vulnerability discovery and active exploitation, AI has compressed that window dramatically. With attackers gaining access to the same advanced tools as defenders, projects face heightened risks and must rethink how they secure protocols and incentivize rapid, responsible disclosures.
What Amador said: coverage limits, AI parity, and payouts
Amador told Decrypt that Immunefi’s AI auditor can outperform most firms but similar capabilities are now within reach of well-funded adversaries, including Lazarus. He argued bug bounties have “hit the limits” because there aren’t enough expert “eyeballs” to cover the expanding attack surface, even as Immunefi-facilitated payouts have surpassed $100 million.
He added that AI has made targeted phishing “pennies per call,” enabling at-scale impersonation and rapid follow-on compromise especially when combined with quotas-driven operator incentives documented in recent threat intelligence.
The Bybit inflection point: it wasn’t the smart contracts
Security post-mortems indicate the February Bybit incident (≈$1.4–$1.5B) subverted transaction approval via a Safe{Wallet} front-end/UI path deceiving signers rather than breaking contract logic. Analysts say the attack altered what approvers saw, leading to valid signatures on malicious transactions. That bypass exposes gaps in infra, signer workflows, and UX that audits/bug bounties alone won’t catch. NCC Group
Chainalysis’ 2024 data also shows shifting targets and persistent DPRK-linked activity, reinforcing why infra-, key-, and process-layer defenses matter as much as code audits.
Where bug bounties still fit
HackenProof’s Dmytro Matviiv told Decrypt manual audits remain vital for subtle, context-heavy issues that AI misses. The likely path forward is hybrid: external researchers + AI scanning + continuous monitoring + hardening of CI/CD and multi-sig operations. Decrypt
Defenses and the road ahead for AI-driven crypto hacks and bug bounties
Immunefi says it’s embedding AI into GitHub and CI/CD to catch vulnerabilities pre-production and is piloting guarded multi-sig workflows that mandate human review for high-risk transactions measures Amador believes could sharply reduce DeFi incidents over the next 1–2 years.
Why AI-driven crypto hacks and bug bounties are at an inflection point
Economics
AI slashes recon/exploit costs; defenders must push detection left (pre-commit, PR, CI).Vectors
The biggest losses now often follow infra/UI compromise and key misuse—not contract bugs alone.Ops security
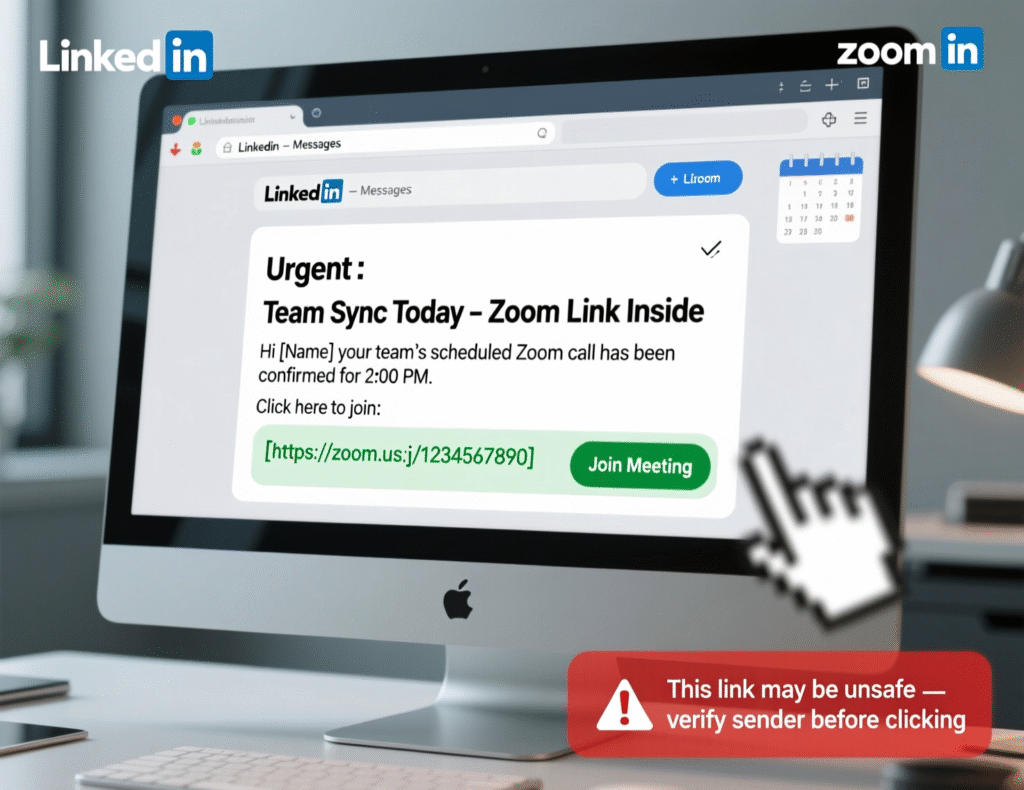
BitMEX’s thwarted LinkedIn/Zoom-style lure shows how basic but scalable phishing remains an entry point.Adversary incentives
Competitive quotas inside DPRK operations encourage rapid, uncoordinated exploitation cycles.
<section id=”howto”> <h3>How to harden your crypto stack before the audit</h3> <ol> <li id=”step1″><strong>Step 1:</strong> Enforce least-privilege, hardware-backed keys for signers; disable blind signing in multi-sig flows.</li> <li id=”step2″><strong>Step 2:</strong> Gate high-value transactions with out-of-band review (4-eyes) and policy engines tied to risk thresholds.</li> <li id=”step3″><strong>Step 3:</strong> Shift-left with SAST/DAST + dependency pinning in CI/CD; block merges on critical findings.</li> <li id=”step4″><strong>Step 4:</strong> Embed runtime monitors (on-chain anomaly detection) and automatic pausers/kill-switches.</li> <li id=”step5″><strong>Step 5:</strong> Phishing-resilience: FIDO2 for all staff, allow-list only access to SaaS/devops, and strict third-party app controls.</li> <li id=”step6″><strong>Step 6:</strong> Practice signer UX drills: verify decoded tx details, addresses, and operation type before approval.</li> <li id=”step7″><strong>Step 7:</strong> Stage an incident-response tabletop covering key compromise, front-end tamper, and bridge exploits.</li> </ol> <p><em>Note: Process may vary by jurisdiction/provider. Confirm requirements before acting.</em></p> </section>
Context & Analysis
The pattern emerging from Bybit and other large incidents is adversaries working “around” smart contracts: UI supply chain, deployment pipelines, and key custody. With AI compressing attacker timelines, coverage-based controls (audits/bug bounties) can’t be the only line of defense; teams need deterministic policy enforcement at sign time, tamper-evident releases, and continuous surveillance to catch drift.
Conclusion
Bug bounties still matter, but they can’t stand alone against AI-accelerated attacks that strike deeper at the infrastructure layer. The threat landscape is evolving too quickly for traditional bounty programs to cover every gap on their own.
The more effective near-term approach is a unified security stack. This means pushing defenses earlier through shift-left automation, strengthening signer user experiences, and ensuring human oversight for high-risk actions. In this model, bug bounties remain important but serve as a complementary safety net for edge cases rather than the primary shield against increasingly complex exploits.
FAQs
Q1 . What does Immunefi mean by bug bounties hitting their limits?
A . Coverage and speed: there aren’t enough expert reviewers to match AI-accelerated attacker timelines, so issues must be caught earlier in CI/CD and signer workflows.
Q2 . Did the Bybit hack exploit smart contracts?
A . Evidence points to front-end/approval-flow manipulation around Safe{Wallet} that deceived signers, not a contract bug.
Q3 . How much was stolen in 2024, and who led the biggest attacks?
A . Chainalysis estimated ~$2.2B stolen in 2024, with DPRK-linked actors responsible for a large share.
Q4 . Are AI-driven crypto hacks and bug bounties incompatible?
A . No. Bounties remain essential for edge cases; they’re shifting into hybrid models alongside automated scanning and runtime monitoring.
Q5 . What’s a practical first step for teams today?
A . Enforce hardware-backed, policy-gated approvals for high-value transactions and disable blind signing; practice out-of-band review.
Q6 . Are social-engineering campaigns actually getting simpler?
A . The lures can be basic (e.g., job offers), but at massive scale—and still effective. BitMEX documented a thwarted Lazarus run.

